Take Advantage Of Cloud Solutions for Enhanced Data Security
Leveraging cloud services presents an engaging option for organizations looking for to strengthen their information protection actions. The concern arises: just how can the use of cloud services change information safety and security practices and provide a durable shield versus prospective vulnerabilities?
Value of Cloud Safety And Security
Making certain robust cloud security procedures is paramount in safeguarding delicate data in today's electronic landscape. As organizations significantly depend on cloud services to store and refine their information, the requirement for solid safety protocols can not be overstated. A breach in cloud safety can have serious consequences, varying from financial losses to reputational damages.
Among the main factors why cloud security is critical is the shared responsibility design employed by the majority of cloud service suppliers. While the service provider is accountable for safeguarding the infrastructure, clients are accountable for safeguarding their data within the cloud. This division of responsibilities highlights the relevance of implementing robust safety and security measures at the individual degree.
Additionally, with the proliferation of cyber risks targeting cloud atmospheres, such as ransomware and data violations, organizations should stay watchful and proactive in mitigating dangers. This includes routinely upgrading safety methods, keeping track of for suspicious tasks, and educating workers on finest practices for cloud security. By focusing on cloud security, companies can better shield their sensitive information and support the count on of their consumers and stakeholders.
Data File Encryption in the Cloud
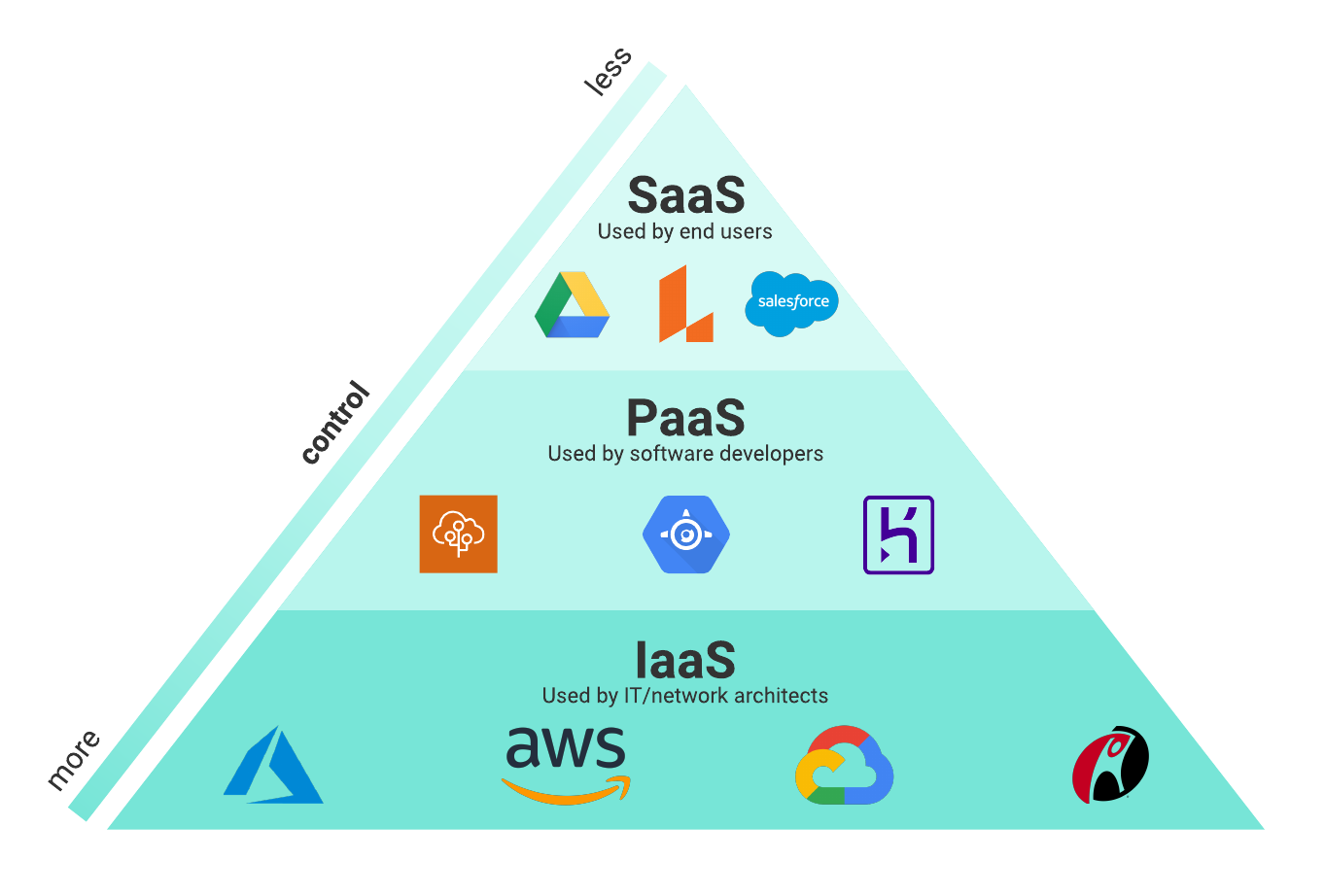
File encryption in the cloud normally includes the usage of cryptographic formulas to clamber data into unreadable formats. This encrypted information can only be analyzed with the equivalent decryption trick, which adds an added layer of safety and security. In addition, numerous cloud company supply encryption mechanisms to safeguard data at rest and in transportation, enhancing general data security. Executing durable file encryption methods together with other safety steps can considerably reinforce an organization's protection against cyber threats and secure beneficial info saved in the cloud.
Secure Data Back-up Solutions
Information back-up solutions play an essential role in making certain the durability and safety and security of information in the event of unforeseen incidents or data loss. Protected data backup why not try this out remedies are vital parts of a durable information security method. By consistently supporting data to safeguard cloud web servers, companies can mitigate the risks related to data loss due to cyber-attacks, hardware failures, or human error.
Implementing protected data backup remedies involves choosing trustworthy cloud solution suppliers that supply file encryption, redundancy, and data integrity actions. Furthermore, information honesty checks make sure that the backed-up information Check Out Your URL stays unchanged and tamper-proof.
Organizations needs to develop automated backup timetables to make certain that data is consistently and successfully supported without manual treatment. When required, normal testing of data reconstruction procedures is likewise vital to assure the effectiveness of the back-up services in recovering data. By spending in protected information backup remedies, organizations can improve their data safety and security posture and lessen the influence of possible information breaches or interruptions.
Duty of Accessibility Controls
Carrying out rigorous gain access to controls is imperative for keeping the protection and integrity of delicate info within organizational systems. Access controls act as a crucial layer of protection against unauthorized access, ensuring that just licensed people can see or adjust delicate data. By specifying who can accessibility specific resources, companies can limit the risk of data violations and unapproved disclosures.

Consistently assessing and updating accessibility controls is vital to adapt to organizational adjustments and progressing safety risks. Continual surveillance and auditing of access logs can aid discover any dubious tasks and unauthorized access attempts promptly. On the whole, durable access controls are fundamental in safeguarding sensitive information and mitigating security threats within organizational systems.
Compliance and Regulations
Routinely guaranteeing compliance with relevant guidelines and standards is essential for companies to support information safety and security and privacy procedures. In the realm of cloud solutions, where data is often saved and refined externally, adherence to industry-specific guidelines such as GDPR, HIPAA, or PCI DSS is important. These regulations mandate certain data handling techniques to protect delicate info and guarantee user privacy. Failure to abide by these laws can cause severe fines, including penalties and lawful activities, damaging a company's online reputation and depend on.
Several suppliers offer file encryption capabilities, access controls, and audit routes to aid organizations satisfy data safety and security standards. By leveraging compliant cloud solutions, companies can boost their data safety posture while fulfilling regulatory commitments.
Verdict
To conclude, leveraging cloud services for boosted information security is necessary for companies to secure delicate info from unauthorized gain access to and possible breaches. By executing robust cloud safety protocols, including information file encryption, protected backup remedies, access controls, and conformity with policies, organizations can gain from innovative safety steps and experience used by cloud company. This assists minimize risks successfully and makes sure the confidentiality, honesty, and availability of information.

Data backup options play a critical duty in ensuring the resilience and protection of data in the event of unforeseen events or data loss. By frequently backing up information to secure cloud servers, companies can alleviate the threats connected with information loss due to cyber-attacks, hardware failings, or human mistake.
Executing safe data backup solutions entails selecting trustworthy cloud solution suppliers that provide file encryption, redundancy, and information integrity measures. By spending in safe and secure information backup options, companies can boost their information safety pose and minimize the influence of potential data violations or disturbances.